Throwback: Phishing lessons from the 2016 US Election
With a new US election looming, let's throwback to the 2016 US election – a crazy event filled with memes, controversies, and, of course, hacking.
At the heart of this election was the hacking of John Podesta's email, the chair of Hillary Clinton's presidential campaign. This was what started the infamous Pizzagate, leading to QAnon and the popularisation of the term 'fake news'. There is something to learn from here. The first email screenshot is what Podesta received. The subsequent ones are from two Clinton campaign employees (an IT guy (CD) and some another campaign worker).
Fake password reset email with a bit.ly link sent to John Podesta
See what's wrong with the email here?
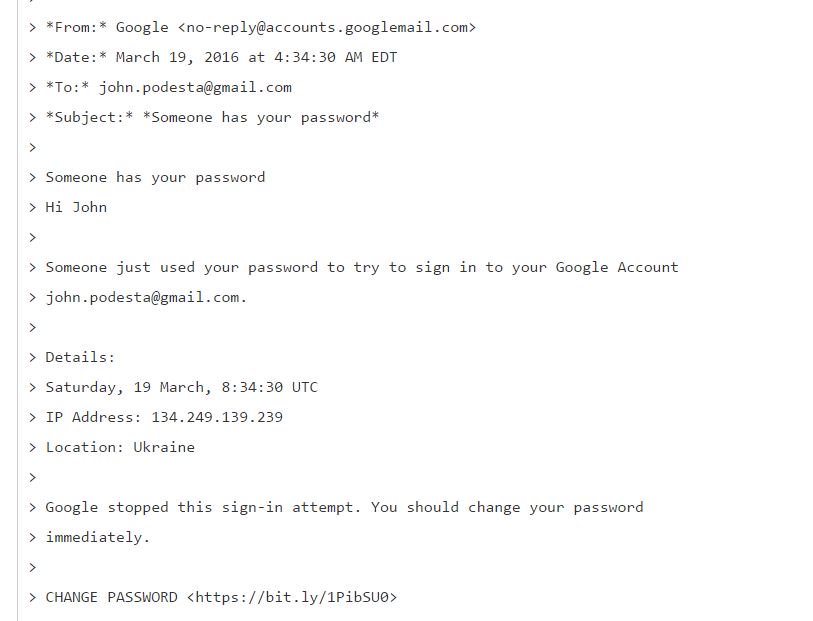
Ok so this email is quite tricky. We see that the sender is [email protected]. The domain is valid. It is not a phishing domain someone quicly registered for $5. The only malicious indicator is the bit.ly link at the end. What I find strange is how this email ended up in the Inbox directly rather than Spam. Unless Google were somehow compromised, GMail would be able to determine that the email does neither passes the DKIM signature check, nor SPF record checks. We do not have information on where the email ended up. Purportedly this was forwarded to CD by Podesta himself from his Spam directory so he can check the legitimacy.
IT think email is legit, direct Podesta to change password on Google using real link
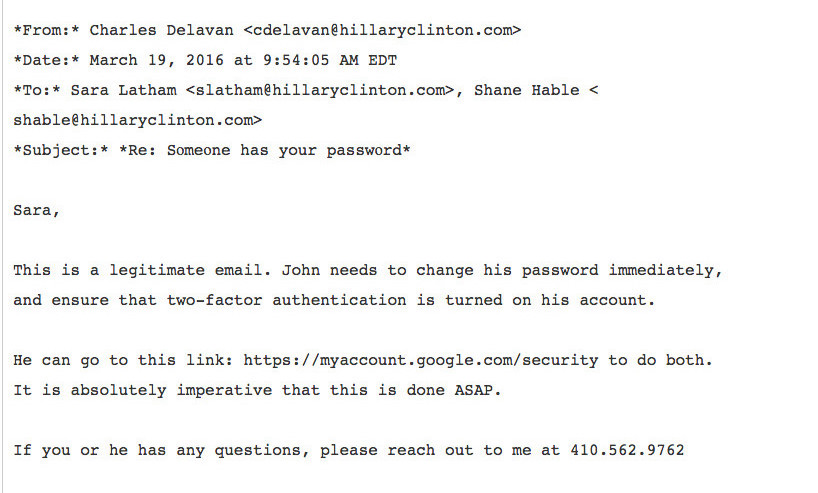
CD got fooled into thinking it is a legitimate email. He tells SL (presumably a person closer to Podesta) that the email is legitimate and he should indeed change his password. What would you have done?
Honestly, if it were me in that exact situation I think I might have done almost the exact same thing, for the following reasons:
- There is a suspicion that someone knows the password of the chief of staff of the person that may become a US president in months.
- The email from address is legit.
- We have zero other warning signs except for the bit.ly link
CD finds and types the correct URL to change the password.
Podesta is directed to change password using "real link"
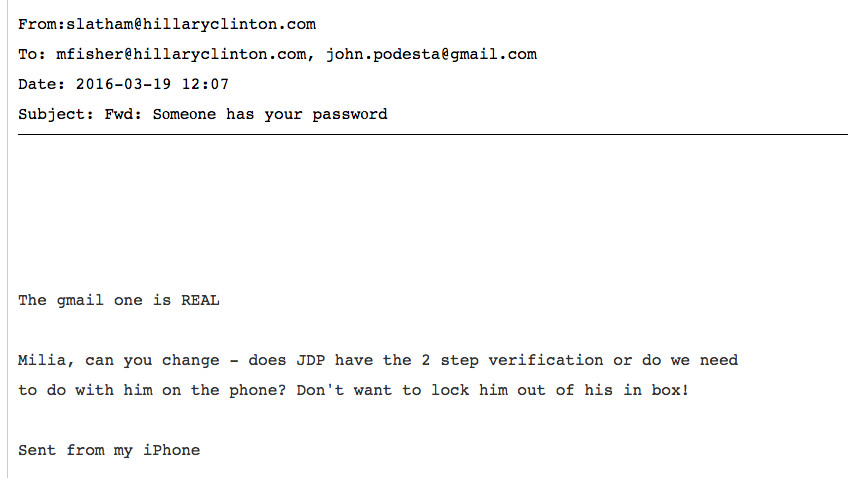
Podesta seemingly uses the bit.ly link to reset his email on a phishing portal. All his emails are downloaded eventually finding their way to wikileaks.
Again, I reiterate that in a high pressure situation where you do not have direct access to the person involved, I would have most likely acted the same. How can you reach the guy if you have no Slack or phone number available?
Still it's a lesson which can help us think.
1. Breathe
If someone sends you an email to be checked it means they are waiting on you. Spending 2 extra minutes to analyse all the email won't exacerbate any situation.
2. We need to speak clearly
The last email to Podesta from one of his other aides says, "The Gmail one is REAL." What on earth does that mean? Which instructions should Podesta follow – the ones in the original phishing email or the one from the IT guy?
A simple call to Podesta, saying "Hey, something strange is going on; reset your Gmail password" would have been ten times better than the communication we see here.
3. Email clients needs to speak human
Terms like DKIM signature not verified or SPF record fail mean absolutely nothing to 99.9% of users. Though in all fairness, nowadays Gmail is doing better by displaying big yellow/red warning boxes.
This is a case of psychology hacking. We are emotional beings and that we act very differently in high pressure situations. It would be very easy to state that the IT guy is an idiot when I'm sitting on my couch, but reality is different. Unless one is experienced you will not be able to
4. Effective security awareness
In 'non-presidential candidate' situations, it is very unlikely that the very act of just clicking on a link will hack your computer or phone. But is it possible? Yes it is. Read about Pegasus malware. I am sure that there are exploits out there that would allow someone to take over your device or computer. These exploits may be already in use or waiting to be discovered. Threat actors being in possession of such high value exploits will not be using this to fire these at everyone. That would lead to the exploit being discovered, and a subsequent patch being developed for it. The exploits that we receive are more of the 0 day exploit kind, where an exploit is made public and bad guys avail themselves of the time for providers to create patch and roll it out.
My point is, even if you click on a link, the sky is (likely) not falling down. Learn to identify domain names clearly. In a URL are you able to identify which is the URL, Domain and URL? Are your users capable of identifying this? I have recently conducted a test, and it's incredible how so many users are unable to pick scammy URLs when given a choice.
Reading a hundred books about swimming does not teach you how to swim. Corporate phishing campaigns in my opinion doing more bad than good (I'll cover why in a separate article). We need to harness characteristics like people's curiosity to deliver security education. Scam stories like the Tinder Swindler and Glibert Chikli were a Netflix hit. As security professionals we need to get off our high horse and start showing how real phishing emails look like, how the scam works and what the end game is. People have stuff to do, our priorities are not theirs.
We need to make security awareness exciting and interesting.
